Join the Cilium Slack
Cilium is an open source project that anyone in the community can use, improve, and enjoy. We'd love you to join us on Slack! Find out what's happening and get involved.
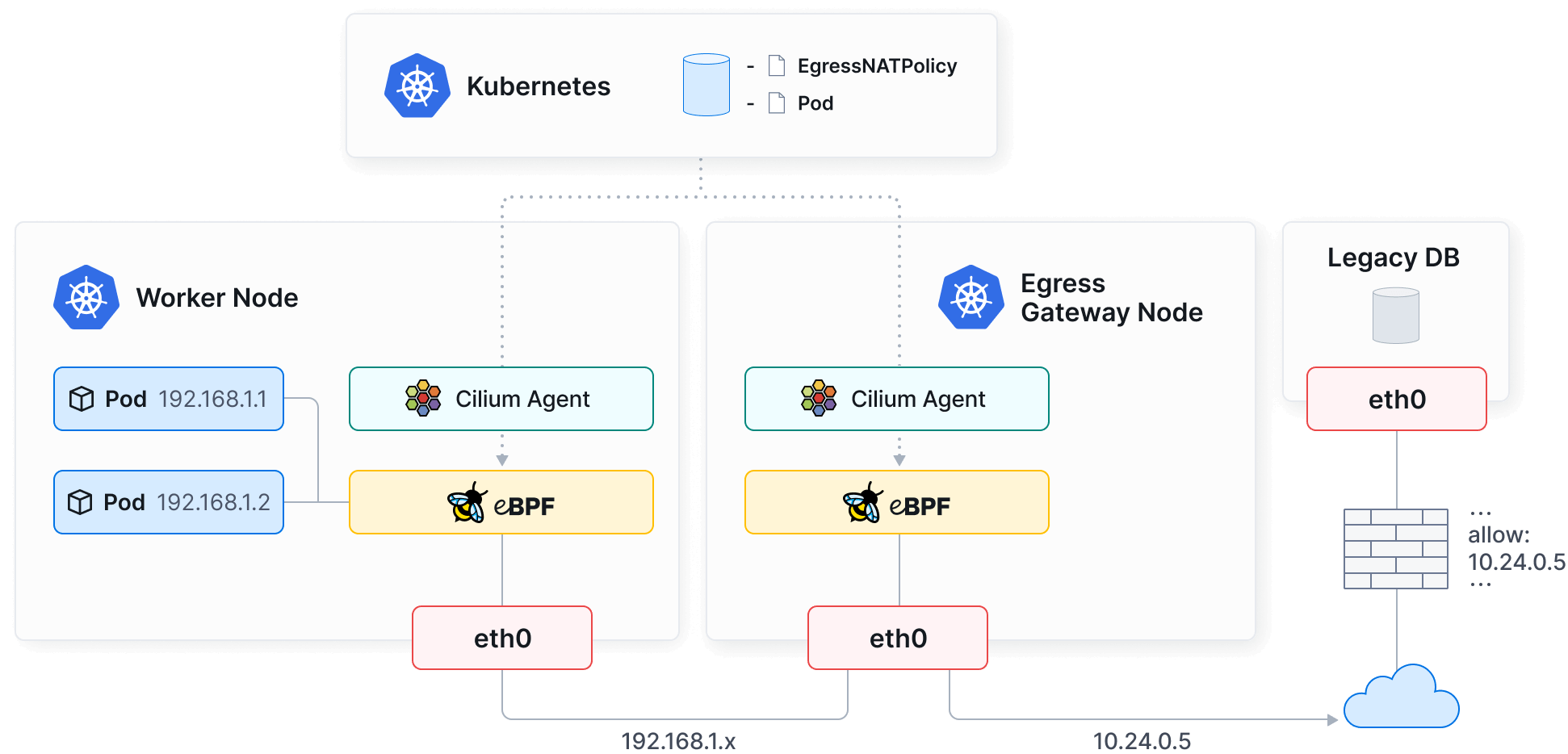
Join the SlackPods typically have ever-changing IP addresses in Kubernetes environments. Even if masquerading is used to mitigate this, the IP addresses of nodes can also change frequently. Egress gateways provide a way to route all outbound traffic from certain pods through a specific node with a predictable IP address. This predictable IP can be useful for scenarios where the traffic destination requires a known source IP, for instance, when working with legacy systems or firewall rules.

Egress Gateway with Cilium fundamentally transforms Kubernetes networking by addressing dynamic IP challenges, ensuring seamless integration with legacy systems and enhancing network security. It provides precise control over traffic routing, enabling selective direction of pod traffic through stable, predictable IP addresses. This feature enables granular traffic management, effective monitoring and filtering, and workload-specific routing, all while facilitating interoperability with systems requiring known source IPs.
The egress gateway allows fine-grained control over which pods' traffic should be routed through the gateway node. This is done by applying egress gateway policies that use label selectors to target specific pods. This selective routing can help in implementing security policies, achieving network isolation, and managing network costs.
In multi-tenant Kubernetes clusters, different workloads might need to interact with different external systems that have specific network requirements. Egress gateways can help meet these requirements by allowing the configuration of workload-specific routing rules.
A telecommunications company implemented a zero-trust networking model on their Kubernetes platform using Cilium's egress gateway. They employed FQDN-based rulesets for flexible blocklisting and a default deny egress policy. To comply with corporate policy, they used a PR-based approval workflow for tenant self-service, underpinned by a two-tier system of CiliumNetworkPolicies (CNPs) and Custom Resource Definitions (CRDs).
Cilium is an open source project that anyone in the community can use, improve, and enjoy. We'd love you to join us on Slack! Find out what's happening and get involved.
Join the SlackCilium has extensive documentation that covers its features and use cases. The docs also features tutorials for common user stories.
Read the DocsGet help with Cilium through Slack, Github, training, support, and FAQs. The community can also help you tell or promote your story around Cilium.
Get Help