Interview: Hubble Integration Added to DigitalOcean Kubernetes
Exclusive Interview with DigitalOcean on Integrating Hubble into their Kubernetes Offering
Exclusive Interview with DigitalOcean on Integrating Hubble into their Kubernetes Offering
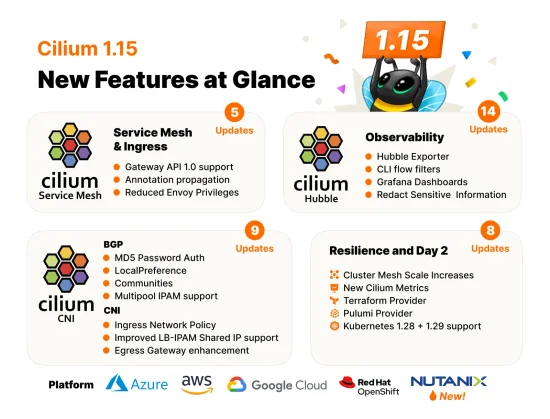
Cilium 1.15 has arrived with Gateway API 1.0 Support, Cluster Mesh Scale Increase, Security Optimizations, and more
There is an amazing lineup of Cilium activities at KubeCon + CloudNativeCon
En introduktion till Cilium
Learn how to set up Tetragon in a Kubernetes cluster
Learn how to deploy a Kubernetes cluster using kubeadm and set up networking with Cilium
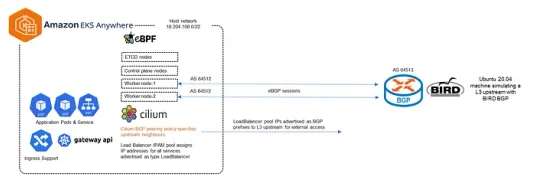
Learn how to replace the default Cilium installation on EKS Anywhere with Cilium
Découvrez comment déployer 511 clusters Kubernetes pouvant communiquer entre eux avec Cilium Cluster Mesh dans un délai raisonnable
Découvrez comment Cilium fonctionne dans l'écosystème Azure Cloud
Learn how to deploy Cilium and Egress Gateway in AKS (Azure Kubernetes Service) using BYOCNI as the network plugin
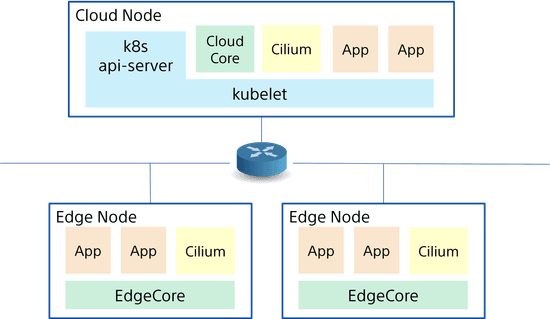
Learn how to how to enable Cilium with KubeEdge
Liz Rice explains why traditional IP-based network policies are becoming outdated and how game-changers like Cilium and eBPF offer more effective and readable policies
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace